Companies are increasingly falling victim to ever more sophisticated cyberattacks. Increasingly, attackers are also using automation technologies. Many companies do not have much to counter these threat scenarios, as the already scarce resources of cyber analysts can only counter the attacks with costly, manual analyses. It's a battle in which enterprises can only lose. Given the lack of incident response and event management expertise, cyber security automation can help organizations manage repetitive security workflows and deliver value in the form of increased cybersecurity.
Cyber Security Automation: What is it?
Cyber security automation enables faster data collection and analysis through the use of artificial intelligence (AI). This, in turn, increases the efficiency and dynamism of incident management. Automated review of myriad data alerts can find many obscure threats that humans don't detect as quickly. Cyber security automation reduces threat volume and enables faster defense against new and previously unknown threats.
It is an excellent tool to better predict behaviors and execute protective measures faster. Cyber Security Automation eliminates the need for manual processing of many time-consuming, repetitive security tasks. This frees up cybersecurity professionals to develop appropriate strategies and initiatives for more complex threat scenarios.
Possibilities of Cyber Security Automation
In order to successfully prevent cyber attacks, cyber security automation offers various possible applications.
Effective data sequencing
Over time, a huge amount of threat data accumulates. However, it only has value for a company if suitable measures can be derived from it. To do this, however, all the threat data collected must be analyzed across all attack vectors and all internal and external threat information in order to identify groups of threats that behave similarly so that the next steps of an attacker can be predicted on this basis. Process automation combined with machine learning (ML) ensure fast, effective and accurate data sequencing and, when combined with dynamic threat analysis, enable the identification of sophisticated, unprecedented threats.
Creation of protective measures
When a threat is identified, speed is of the essence. Protective measures must be created and deployed faster than an attack can propagate through the organization's networks and endpoints. Given the pace at which automated cyberattacks are now being carried forward, manually creating a full set of protections across security technologies should no longer be an option for enterprises. AI-powered automation can speed up the process of creating protective measures without straining resources, while keeping pace with the attack.
Faster than the attacker
Developing protective measures alone is not enough, they must also be implemented and not just at the point of threat, but across the entire infrastructure to prevent the attack from progressing further. The use of cyber security automation in the development and implementation of protective measures is the only remedy against an automated and well-coordinated attack. Automated Big Data attack sequencing and automated generation and distribution of protective measures give organizations the edge to accurately predict the next step of an attack and respond accordingly and quickly.
Early detection of infections
When a threat enters the network, the clock starts ticking down to the security breach. Again, it's all about plugging the security hole quickly before the data leaves the network. The premise here is that you can analyze your data backward and forward in time and look for a combination of behaviors that indicate the system has been infected. As with unknown threat analysis, manually analyzing the context of data on the network is extremely difficult to scale. In the event of a system compromise, security automation provides faster analysis for equally fast intervention.
Benefits of Cyber Security Automation
Cyber Security Automation makes it easier for organizations to deal with the increasing number of security alerts and potential incidents that would take valuable time to resolve. Automation enables security teams to handle potential alerts faster and more effectively. By implementing cyber security automation, automated workflows can be leveraged and processes can be automated to fully automate the triage, investigation and containment processes and perform a variety of granular data enrichment, notification, containment and custom actions based on logical decisions while ensuring that no threat goes unnoticed.
At the same time, the security team still has the authority to decide not only how far automation is implemented into security operations, but also whether to automate both high-risk and low-risk security operations.
All-purpose weapon Robotic Process Automation (RPA)
As part of Cyber Security Automation, Robotic Process Automation performs functions such as scanning, monitoring and low-level incident response. RPA extracts and aggregates data, reduces response time through automated detection and alerts, and helps identify exposed attack surfaces to mitigate security risks. RPA ensures 24/7/365 security coverage and improves security through automated rollout of updates and patches. RPA increases cybersecurity efficiency by taking the burden of manually performing repetitive tasks and helps minimize cybersecurity's biggest vulnerability: human interaction.
But as useful and sensible as the use of RPA is in the context of cyber security automation. It should not be forgotten that RPA reaches its limits when it comes to deeper security processes that require higher cognitive and analytical skills. This part should still be taken over by human analysts in interaction with cognitive learning technologies.
The role of SOAR
With the increasing number of alerts and threats, it is becoming more and more impossible for cyber security experts to deal with each and every one of them. That's why cyber security automation has become more than a nice-to-have. Security Orchestration Automation and Response (SOAR) - as an integral part of cyber security technology - relieves the burden on security departments by automating repetitive behavior and tasks.
The level of automation can be customized in the process. SOAR is a type of technology that enables organizations to automate the analysis of repetitive tasks to better detect, track and remediate potential threats. While security automation focuses on helping teams with repetitive, time-consuming and simple tasks, orchestration allows all required technologies to be connected via API connectors, bringing all necessary information together on a unique SOAR platform.
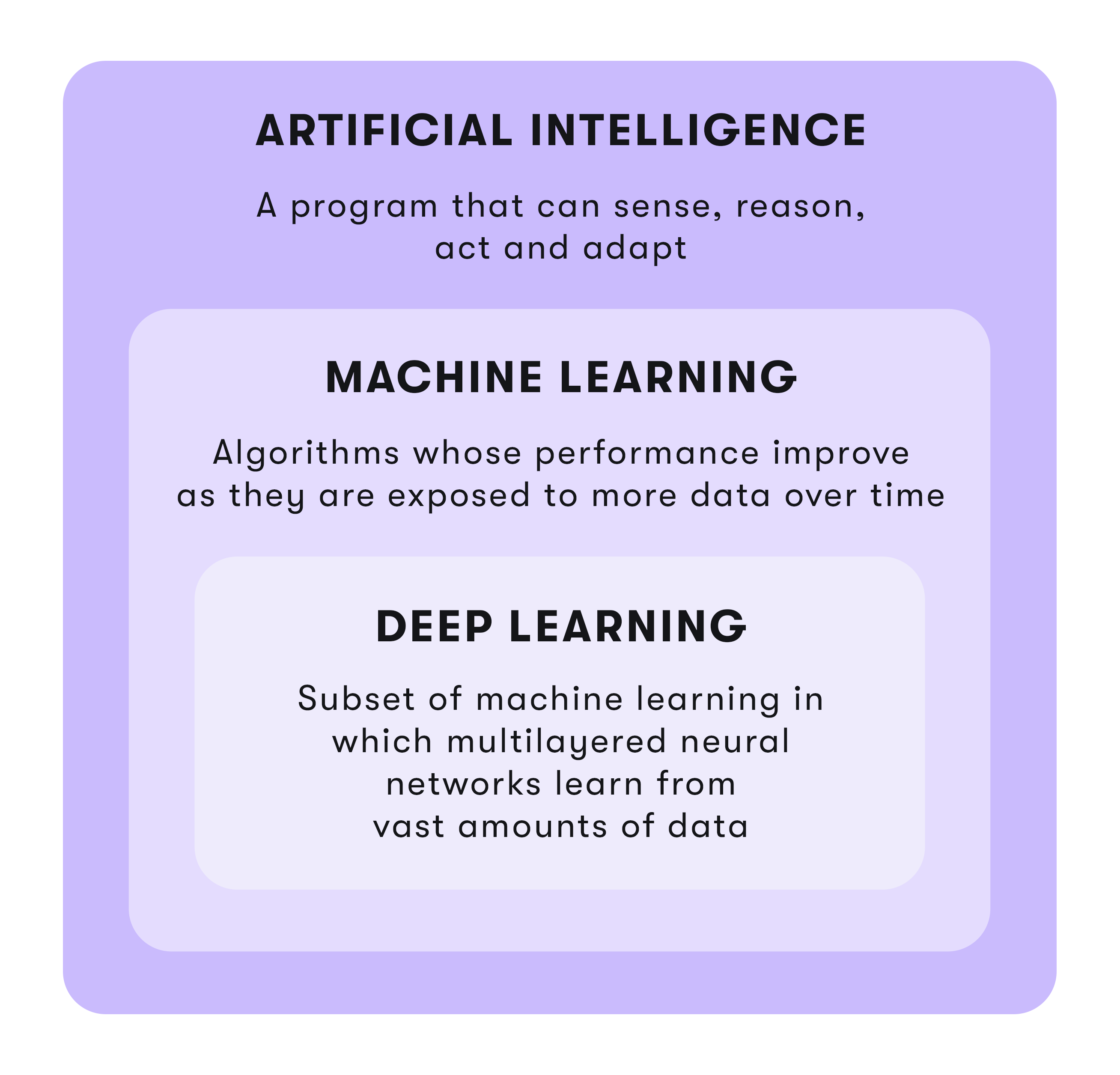
The AI and ML tandem
Integrating artificial intelligence (AI) and machine learning (ML) technologies and processes is designed to improve organizations' analytics capabilities and eliminate tedious, time-consuming cognitive tasks to free up security professionals to focus on higher-priority responsibilities and tasks. AI-based cyber security automation provides up-to-date knowledge of global and industry-specific threats to make critical prioritization decisions based not only on which attack agent could be used to attack the organization, but also based on which attack agent is likely to be used to attack the organization.
Prescriptive insight for greater cybersecurity
With knowledge of IT asset inventory, threat posture, and control effectiveness, AI-based systems can predict how and where organizations are most likely to be attacked so that resource allocation for vulnerabilities can be planned. Prescriptive insights from AI analysis help configure controls and processes to improve enterprise cyber resilience. Such systems provide optimized context for prioritizing and responding to security alerts to ensure rapid incident response and root cause discovery, minimize vulnerabilities, and prevent future problems. AI technologies can identify and prioritize risks, instantly detect any malware on a network, manage incident response, and detect intruders before they cause damage.
Cyber Security Provider
Therefore, Research and Markets experts also predict that the AI cybersecurity market is expected to grow to $38 billion by 2026 from $8.8 billion in 2019. Increasing adoption of Internet of Things (IoT), rising number of connected devices, and increasing instances of cyber threats, increasing vulnerability of Wi-Fi networks to security threats are expected to be the key drivers for the growth of the market in this regard.
Conclusion
Cyber Security Automation analyzes eligible data faster than any human, converts unknown threats into known threats, creates an attack DNA, and automatically enforces full protection across the enterprise to stop the attack. Designed as a reactive model, Cyber Security Automation responds only to cyber threats by optimizing to anticipate familiar behavior and using machine learning and AI to automate specific tasks as directed by analysts. In the proactive model, security analysts decide what form the automation should take in response if a real threat is detected.